Overview
What it Does
Blocking rules are powerful guardrails that allow you to define specific conditions under which pull requests should be blocked from being merged. This helps ensure that your codebase adheres to your organization’s security and quality standards by preventing potentially risky or non-compliant code changes from being merged. You can create two types of blocking rules:- Code Vulnerability Rules: Block PRs based on code security issues found by SAST scanning
- Dependency Vulnerability Rules: Block PRs based on vulnerable dependencies found by SCA scanning
Who it’s For
Blocking rules are primarily designed for:- Development teams
- Project managers
- Security professionals
Key Features and Benefits
Enforce Coding Standards
Enforce Coding Standards
Define rules based on Common Weakness Enumerations (CWEs) to block pull requests that introduce specific types of vulnerabilities or code quality issues.
Customize Urgency Levels
Customize Urgency Levels
Assign urgency levels (e.g., critical, high, medium, low) to different types of issues, allowing you to prioritize and handle them accordingly.
Project-Specific Rules
Project-Specific Rules
Apply blocking rules to specific projects or across your entire organization, giving you granular control over which projects are subject to which rules.
Rule Management
Rule Management
Easily create, edit, and delete blocking rules through a user-friendly interface, ensuring your rules stay up-to-date with your evolving requirements.
Rule Activation/Deactivation
Rule Activation/Deactivation
Toggle the status of blocking rules to temporarily enable or disable them as needed, without losing their configurations.
Rule Types
Blocking rules support two distinct types to provide comprehensive security coverage:Code Vulnerability
Blocks pull requests based on code security issues found by static application security testing (SAST).Configure by:
- Selecting specific CWE (Common Weakness Enumeration) categories
- Setting urgency/severity levels
Dependency Vulnerability
Blocks pull requests based on vulnerable dependencies found by software composition analysis (SCA).Configure by:
- Setting urgency/severity levels (Critical, High, Medium, Low)
How it Works with GitHub
Prerequisite You must have installed and configured the Corgea GitHub App with appropriate repository permissions.
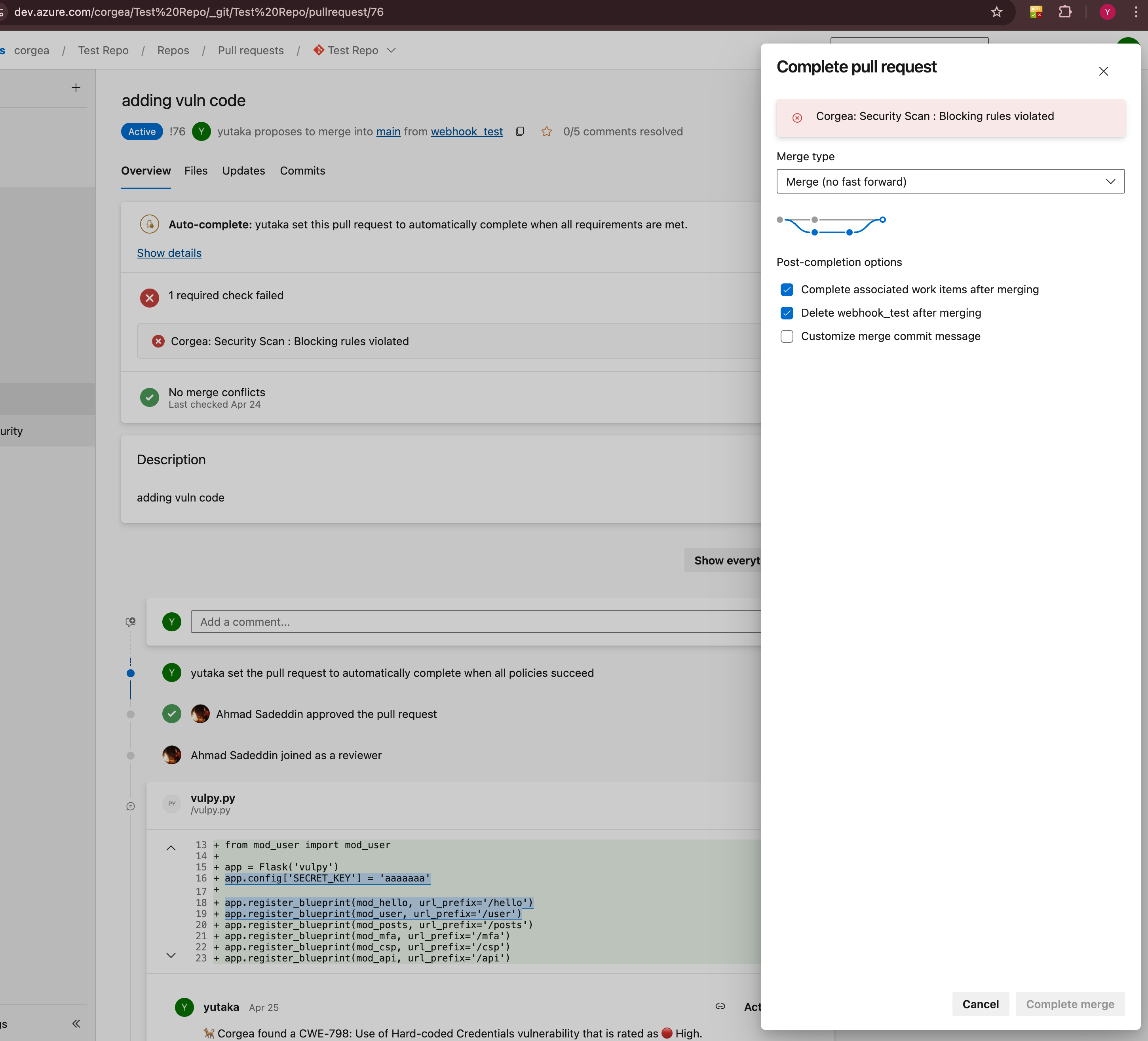
How it Works with Azure DevOps
Prerequisite Make sure the Azure DevOps integration with Corgea is configured and you have the necessary permissions.
Automated Analysis
The system evaluates the code changes against the active blocking rules set in Corgea.
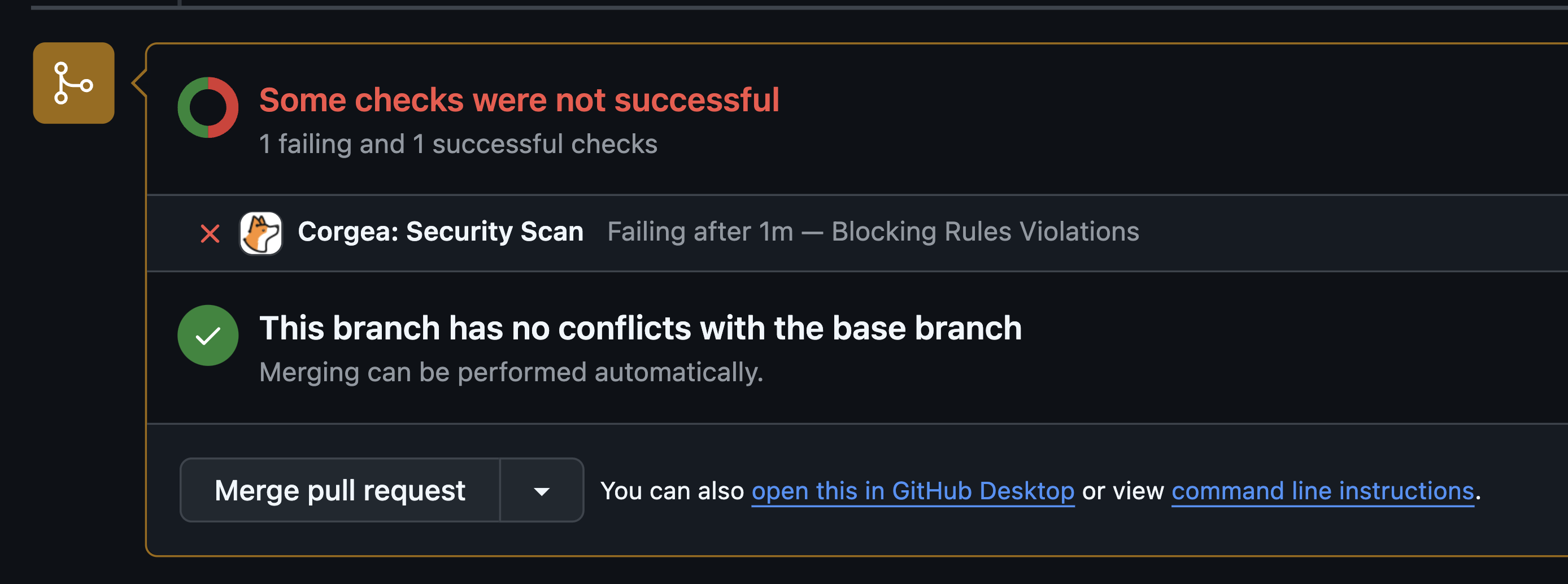
Rule Validation
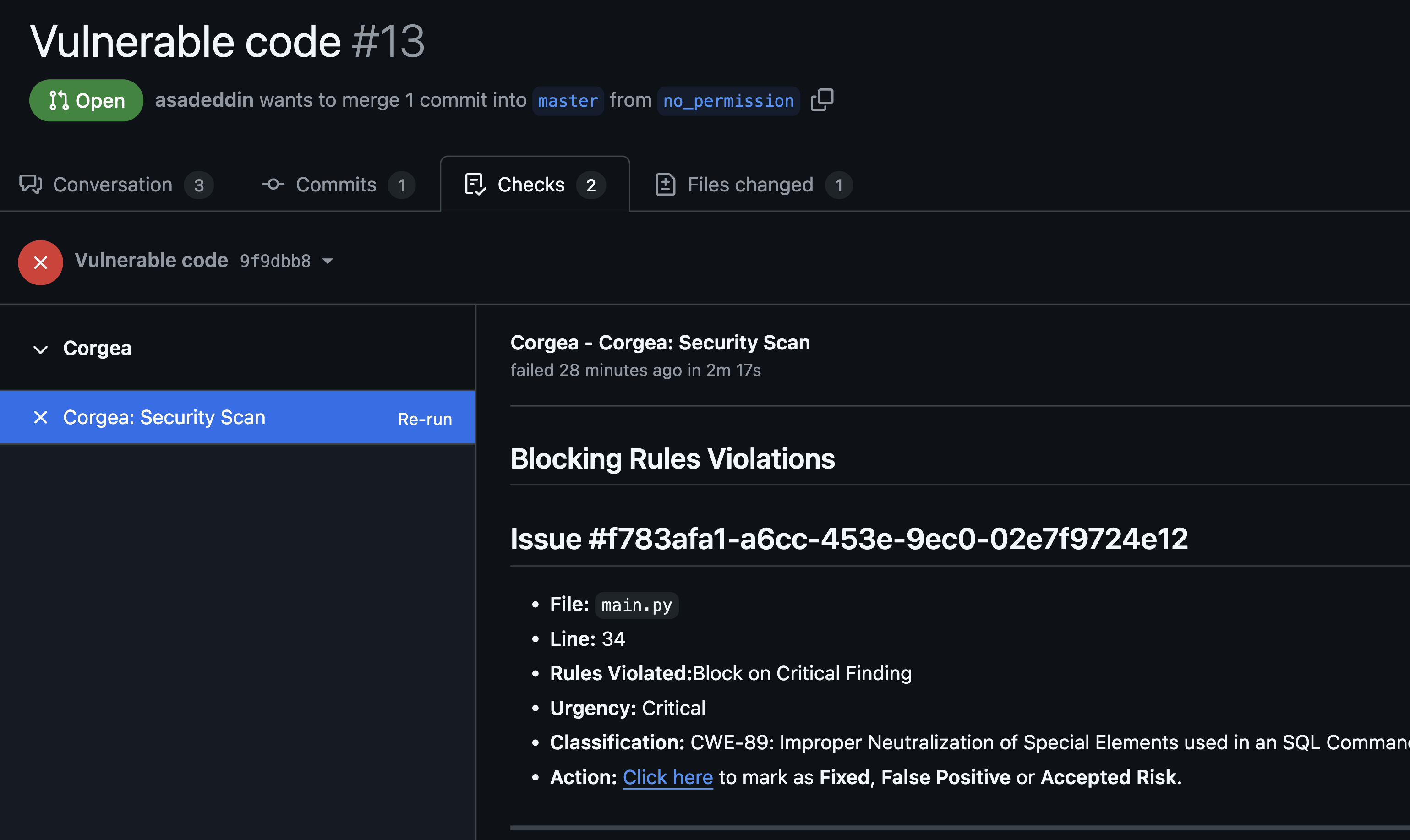
If violations are found, the pull request is automatically blocked.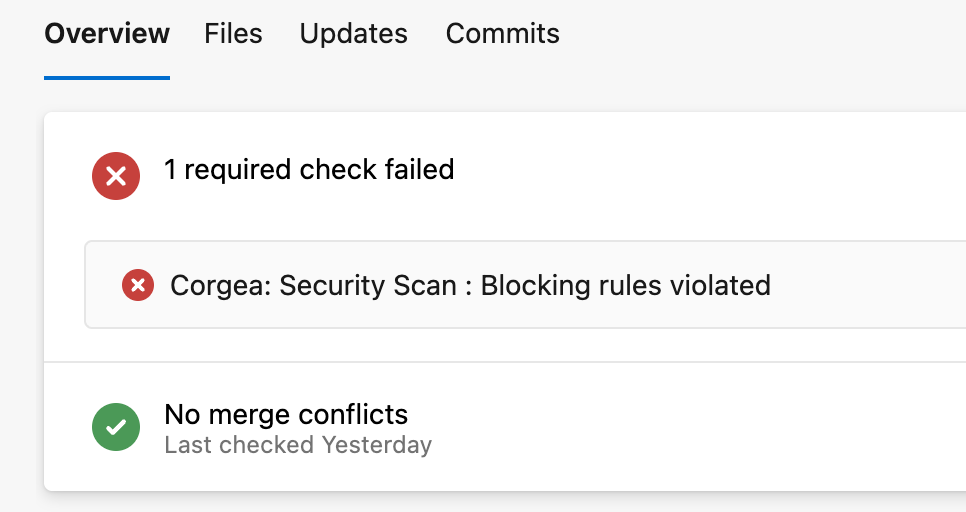


Developer Notification
The developer receives a link to view detailed information about the failed issues on the Corgea Scan page.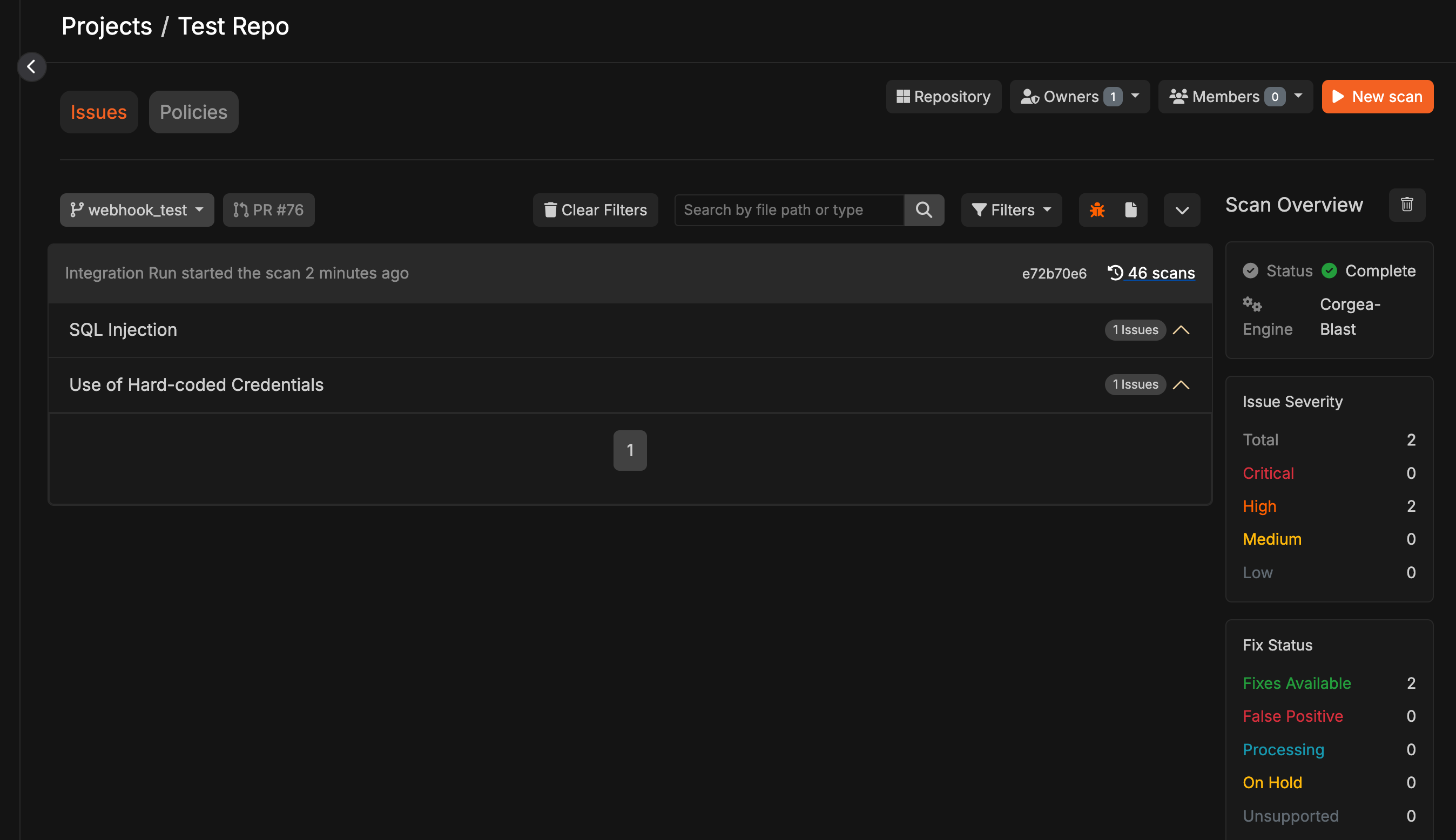

Usage Guide
Creating a New Blocking Rule
Choose Rule Type
Select the type of blocking rule: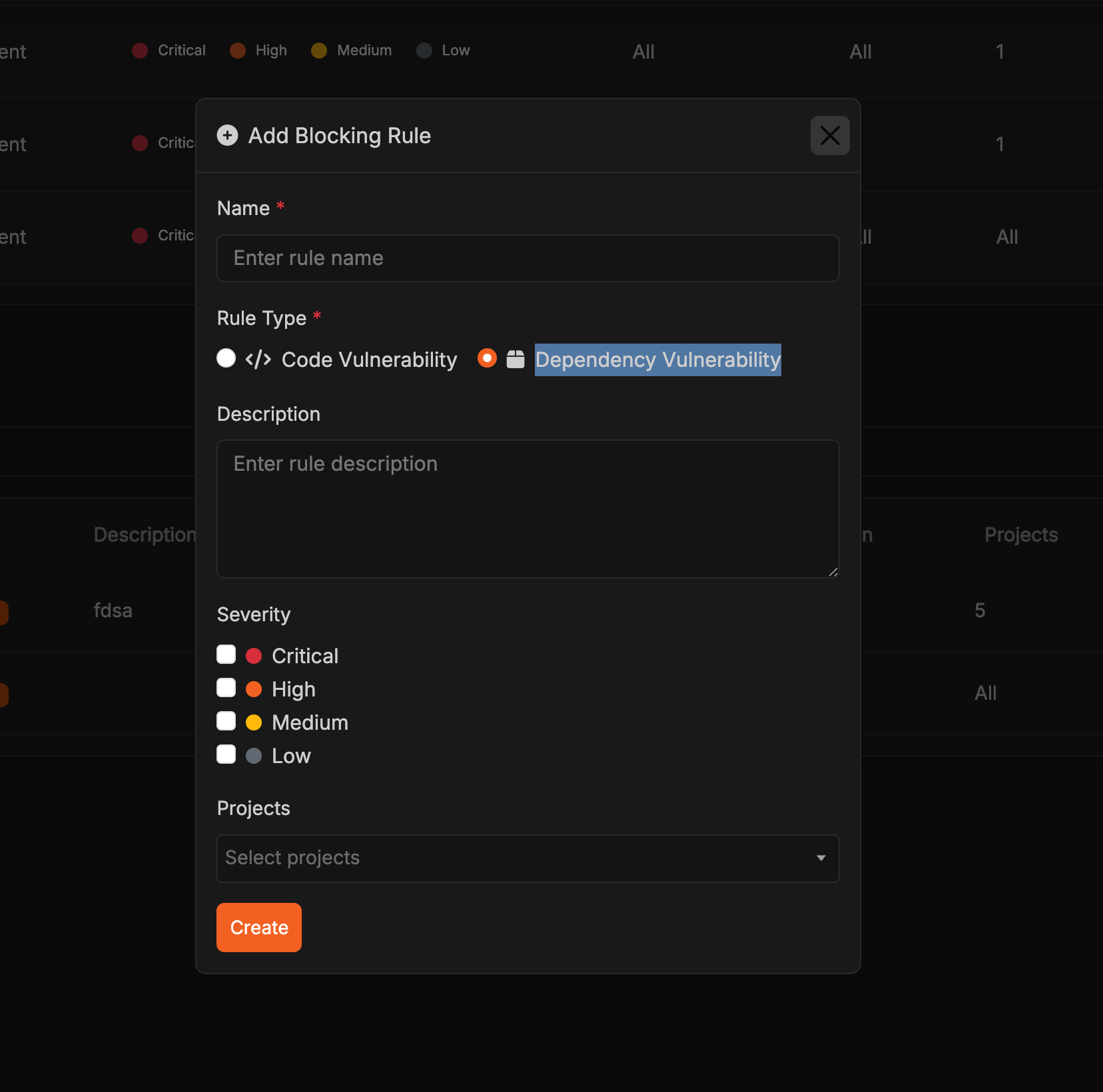
- Code Vulnerability: Block pull requests based on code security issues (SAST findings)
- Dependency Vulnerability: Block pull requests based on vulnerable dependencies (SCA findings)

Configure Settings
For Code Vulnerability rules: Select urgency levels (Critical, High, Medium, or Low) and/or target CWEs - at least one of these must be defined for the rule to be validFor Dependency Vulnerability rules: Select urgency levels (Critical, High, Medium, or Low) to block pull requests with vulnerable dependencies matching those severity levels
Managing Existing Rules
- Edit Rule
- Toggle Status
- View Details
- Locate rule in table
- Click “Edit” button
- Modify settings as needed
- Click “Update” to save
Viewing Rules on scans
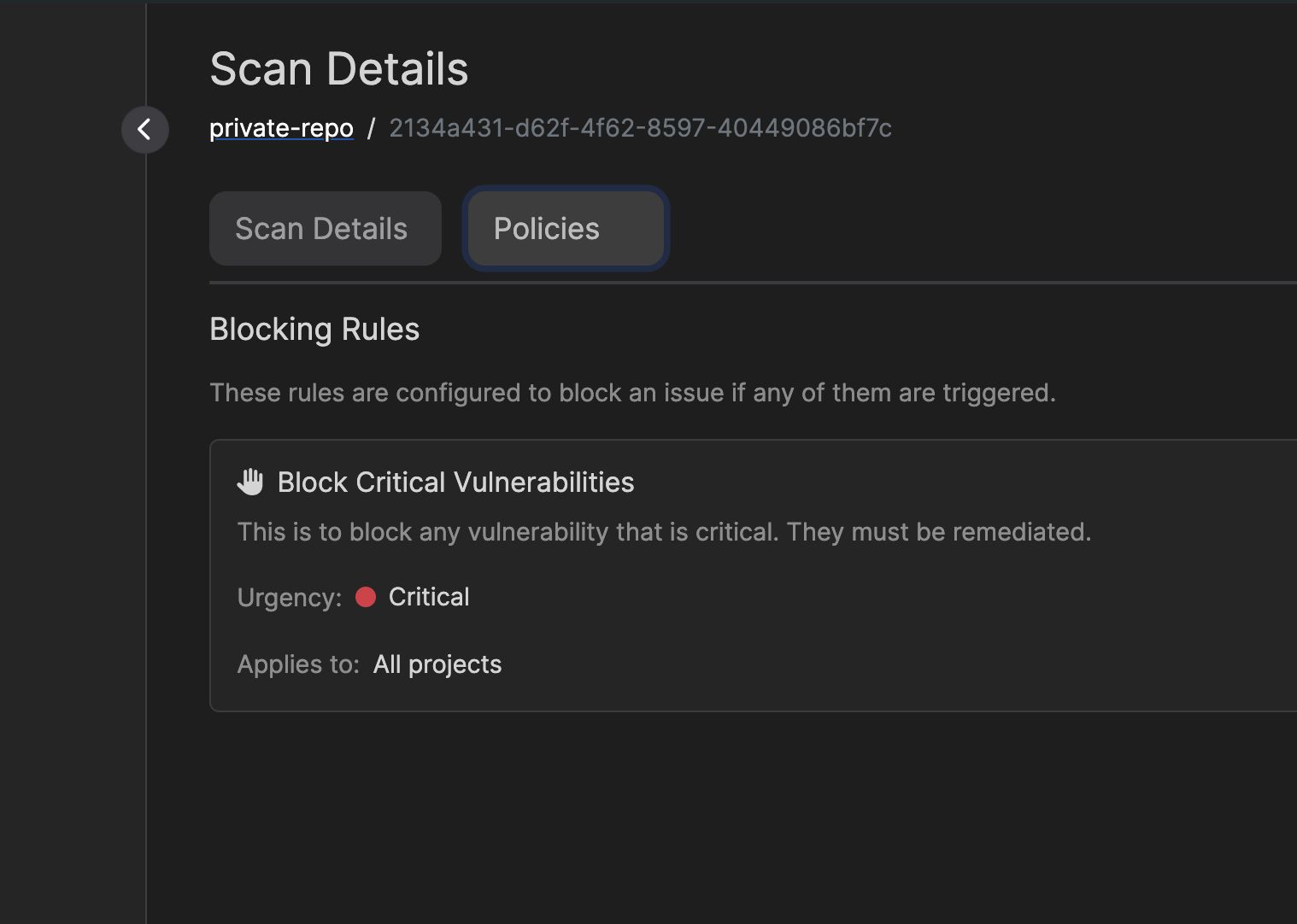
You can view blocking rules that apply to your scans in two places:- On the scan details page, you’ll see a “Blocking Rules” section showing all rules that were evaluated:
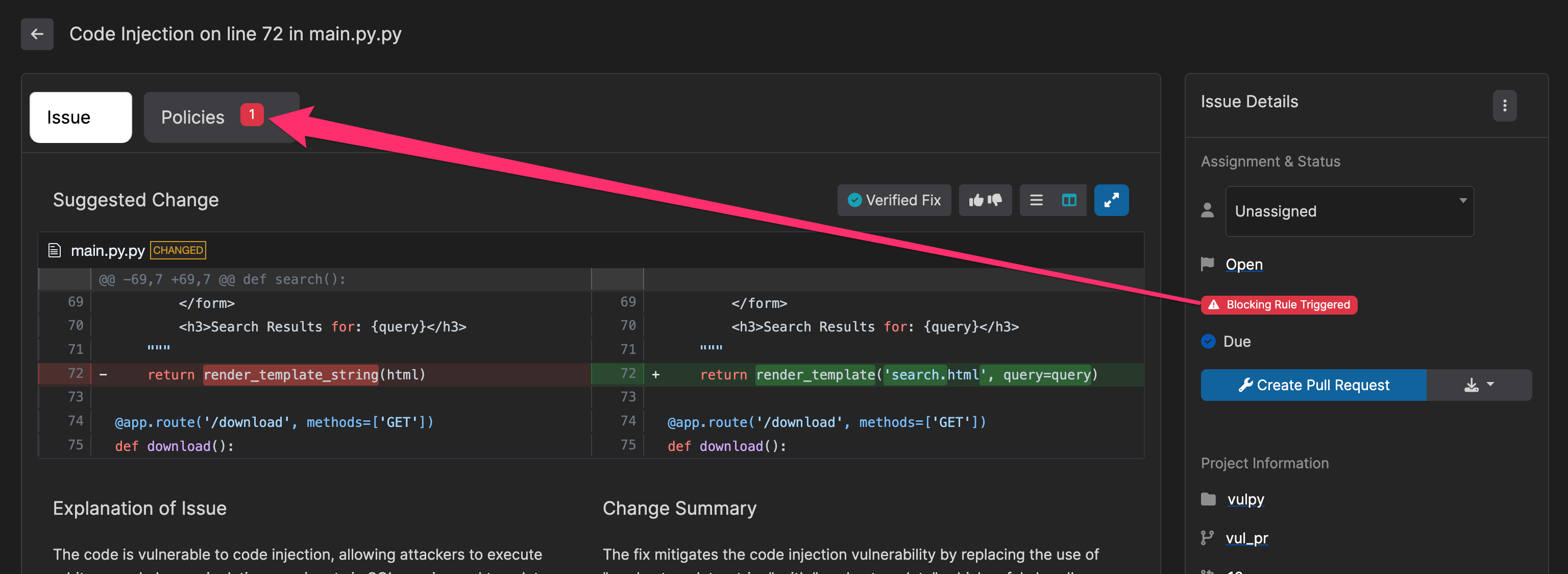
- For individual issues, you can see which blocking rules were triggered in the issue details:
Examples
Blocking Insecure Cryptography
Blocking Insecure Cryptography
Rule Type: Code VulnerabilityCreate a rule targeting CWE-326 (Inadequate Encryption Strength) and CWE-327 (Use of a Broken or Risky Cryptographic Algorithm) with “Critical” urgency to prevent weak encryption usage.
Enforcing Code Quality
Enforcing Code Quality
Rule Type: Code VulnerabilitySet up a rule for CWE-398 (Indicator of Poor Code Quality) and CWE-477 (Use of Obsolete Functions) with “Medium” urgency to maintain code standards.
Blocking Critical Dependency Vulnerabilities
Blocking Critical Dependency Vulnerabilities
Rule Type: Dependency VulnerabilityCreate a rule with “Critical” and “High” urgency levels selected to automatically block any pull request that introduces dependencies with critical or high-severity vulnerabilities. This ensures your supply chain remains secure and prevents known vulnerable packages from entering your codebase.
Best Practices
Implementation Tips
- Start with essential rules and gradually expand
- For Dependency Vulnerability rules, begin with Critical severity only, then add High as your team adjusts
- For Code Vulnerability rules, focus on the most impactful CWEs first (e.g., injection flaws, authentication issues)
- Regular review and updates
- Clear documentation and team training
- Encourage feedback and collaboration
- Strategic use of urgency levels
- Consider creating separate rules for different project types or teams
Troubleshooting
Common Issues
Common Issues
- Unexpected blocking behavior
- Rule targeting issues
- Project scope problems
Resolution Steps
Resolution Steps
- Check rule configurations
- Verify CWE targeting
- Confirm project settings
- Contact support if needed