Generate an Azure DevOps Personal Access Token
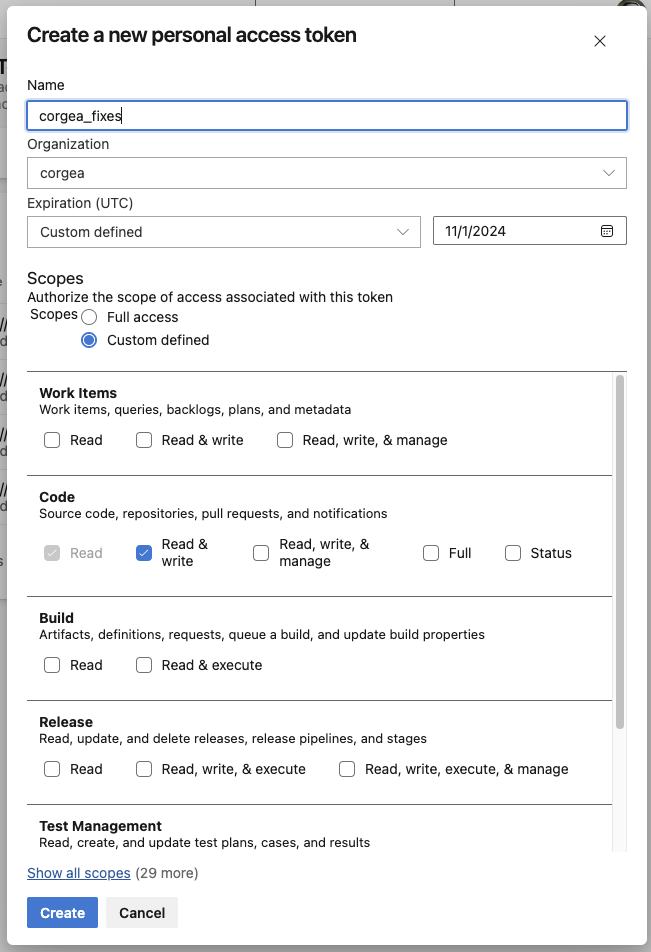
Access your Azure DevOps account and generate a personal access token (PAT) with both read and write permissions.


Integrate the Token with Corgea
Proceed to the Integrations page on Corgea. Click the ”+” button within the Azure DevOps section and ensure the token is securely saved.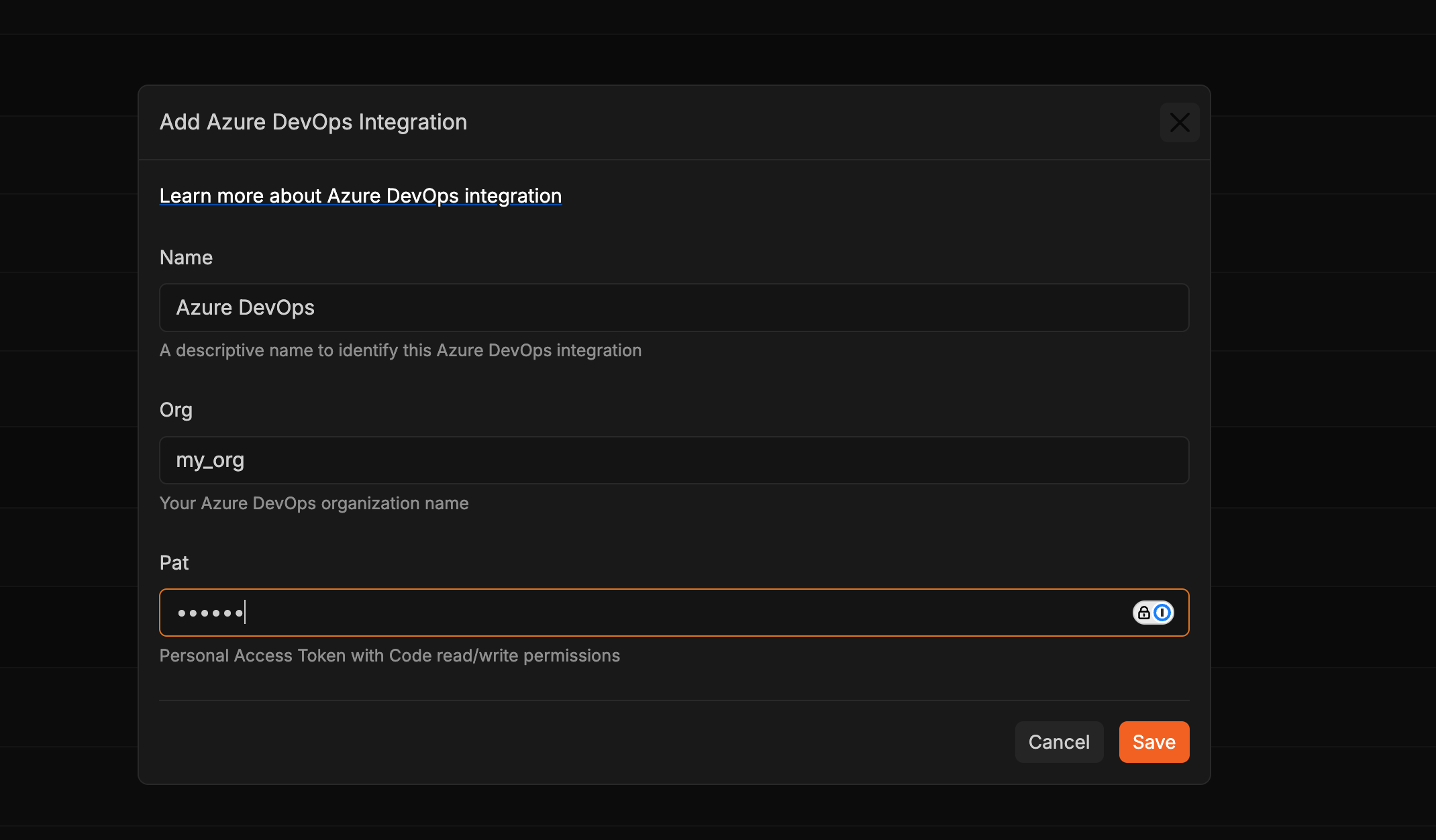

Identify Azure DevOps Projects in Corgea
After configuration, navigate to the Projects page. Your Azure DevOps project will be displayed with a Windows icon. Click the ”+” in the action column to initiate the first scan, or select the project name and click “New Scan” to commence a new scan.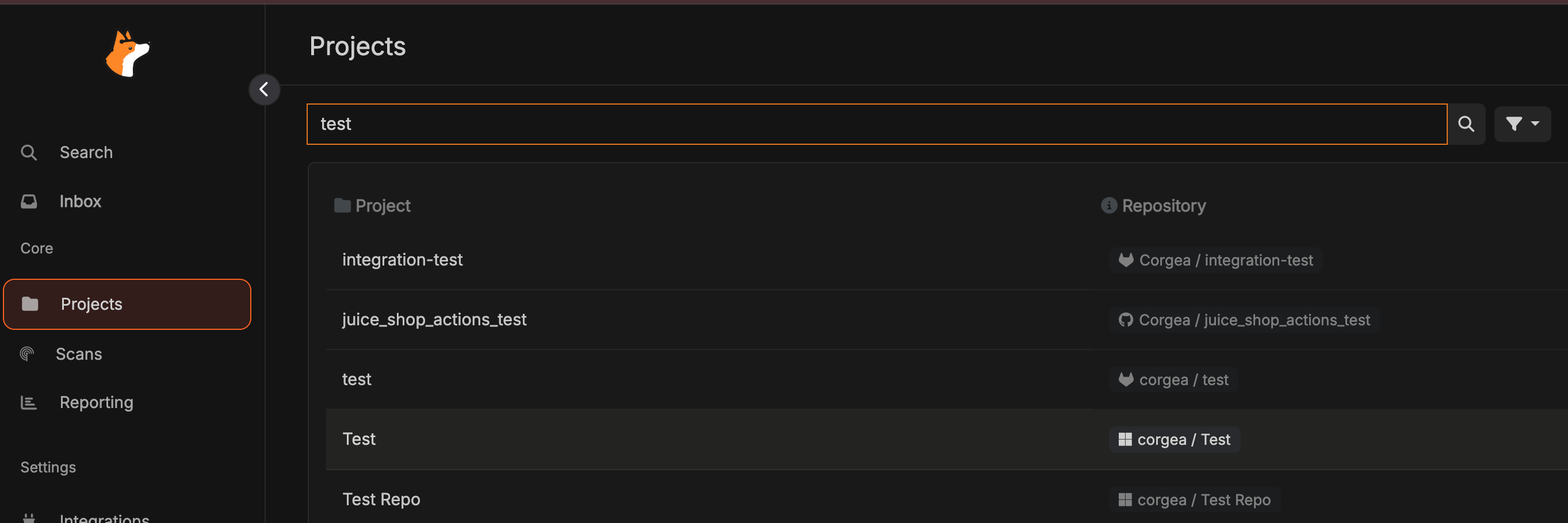

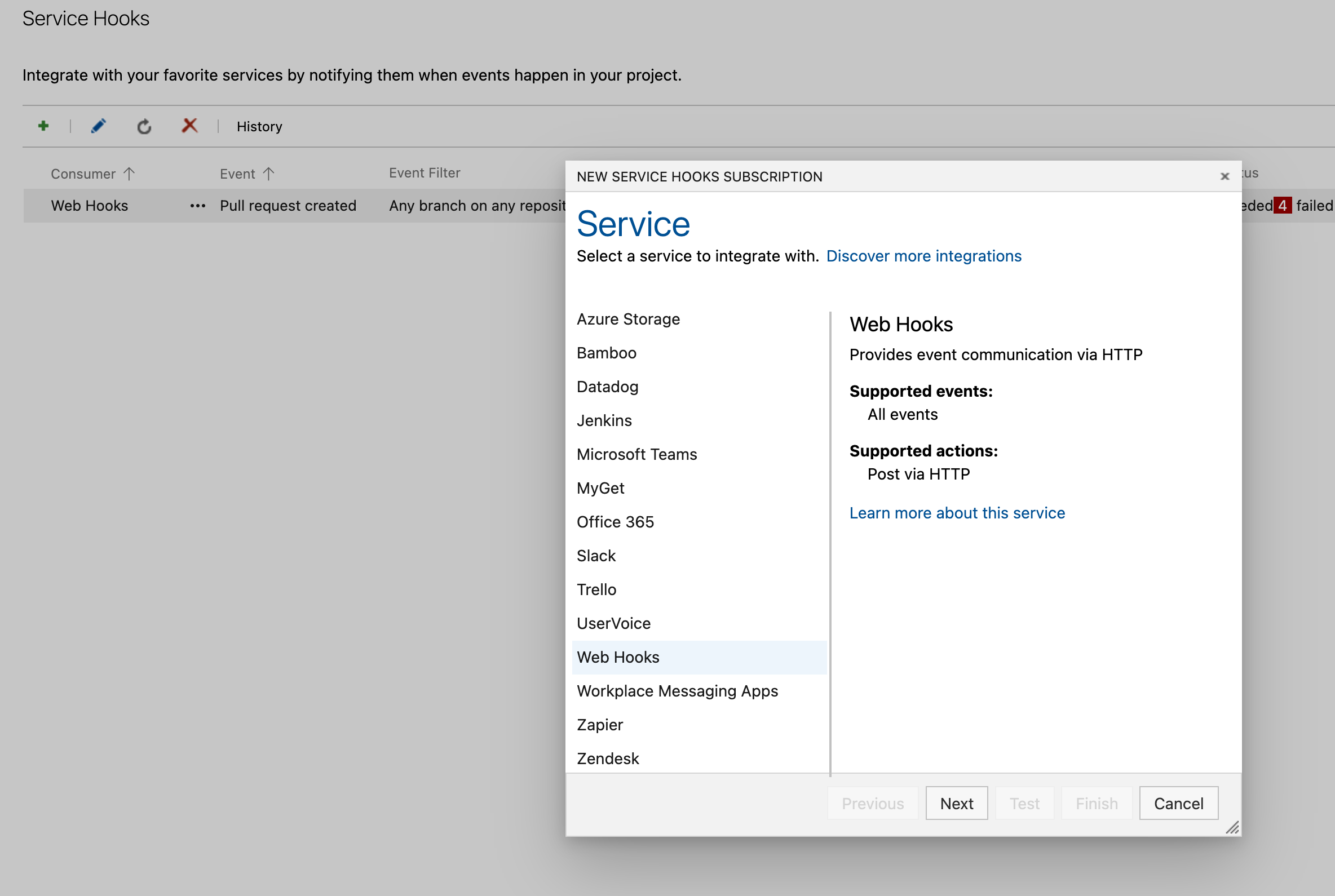
Optional: Webhook Configuration
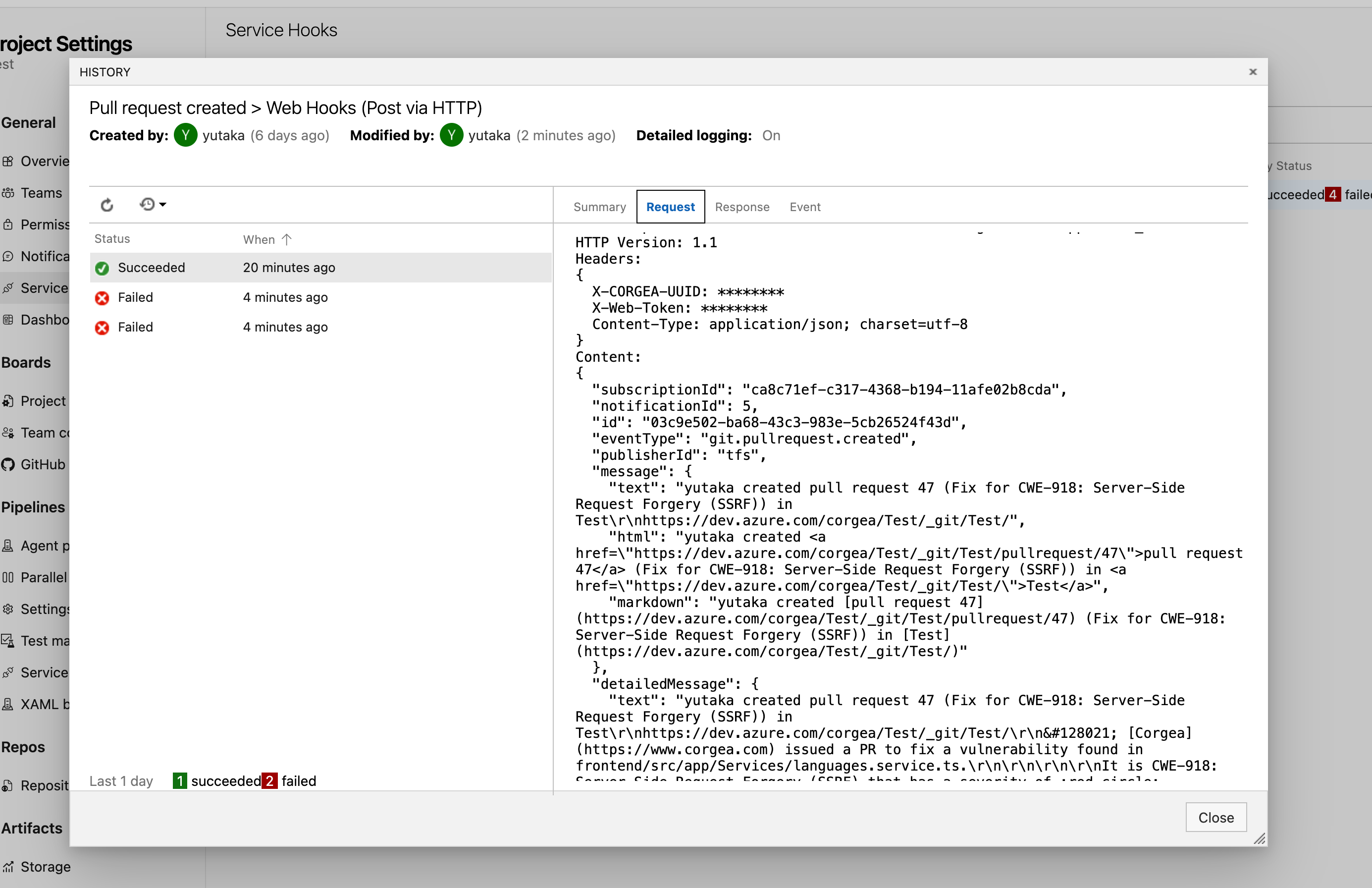
To enable scans for each pull request, configure a webhook. Ensure you possess the requisite permissions to set up webhooks for your project.Select “Pull request created” as the trigger event, configure any optional settings, and click “Next”.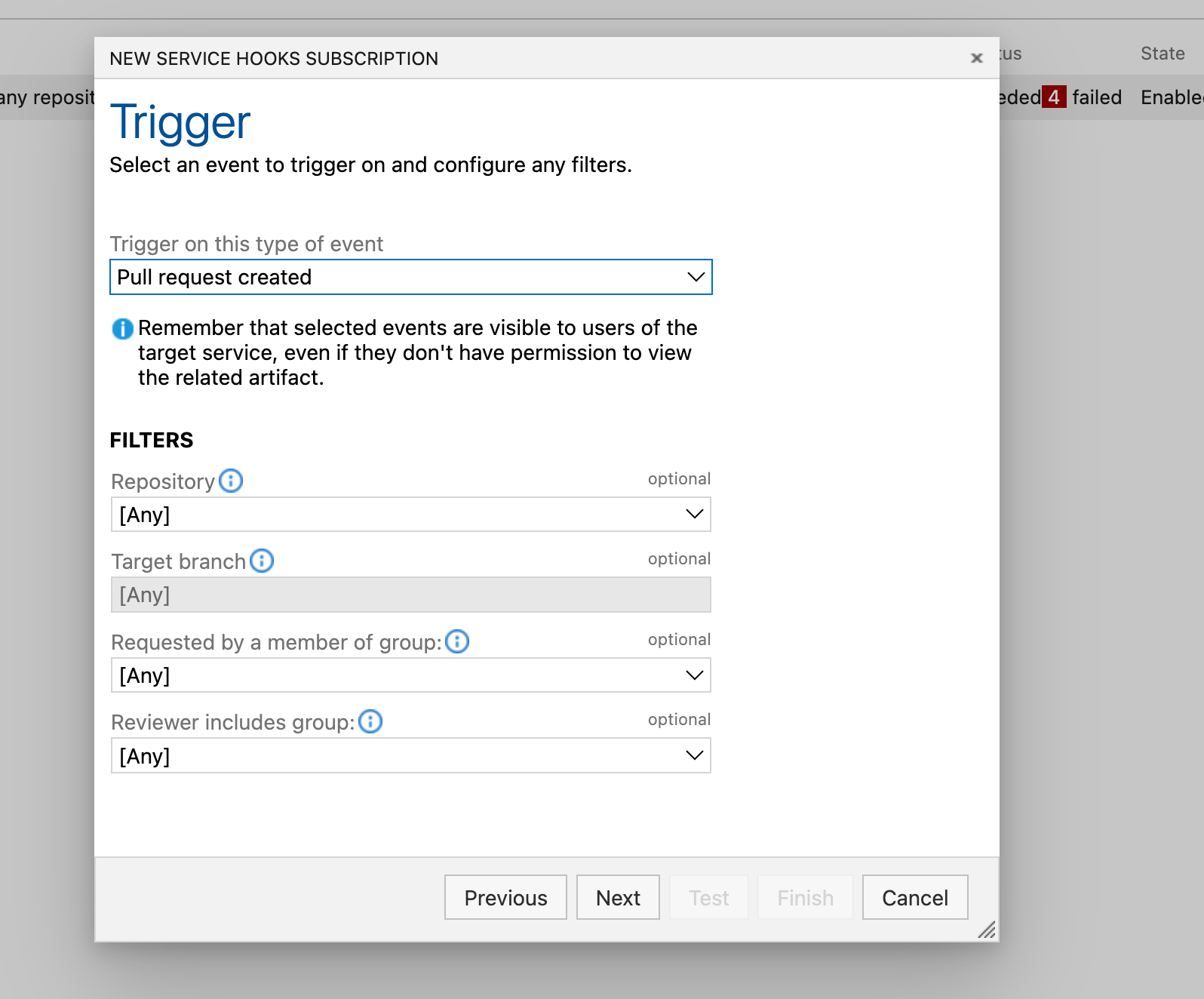

In the Settings section, input the URL as https://www.corgea.app/azure_webhook/ or 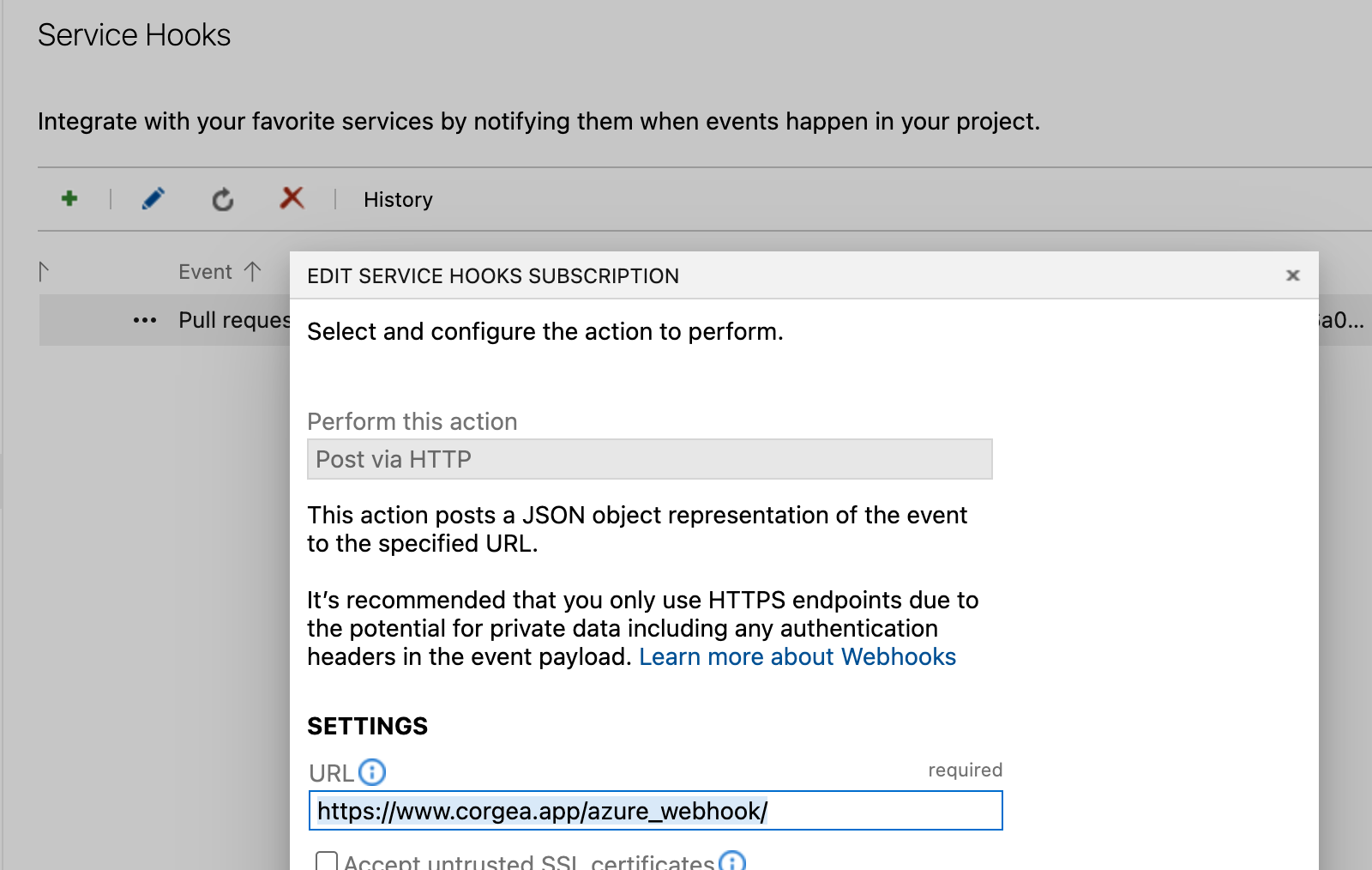
https://your_instance.corgea.app/azure_webhook/ for private deployments.
Open a new browser tab, navigate to the Corgea integrations page, and locate your Azure integration. Copy the X-CORGEA-UUID value.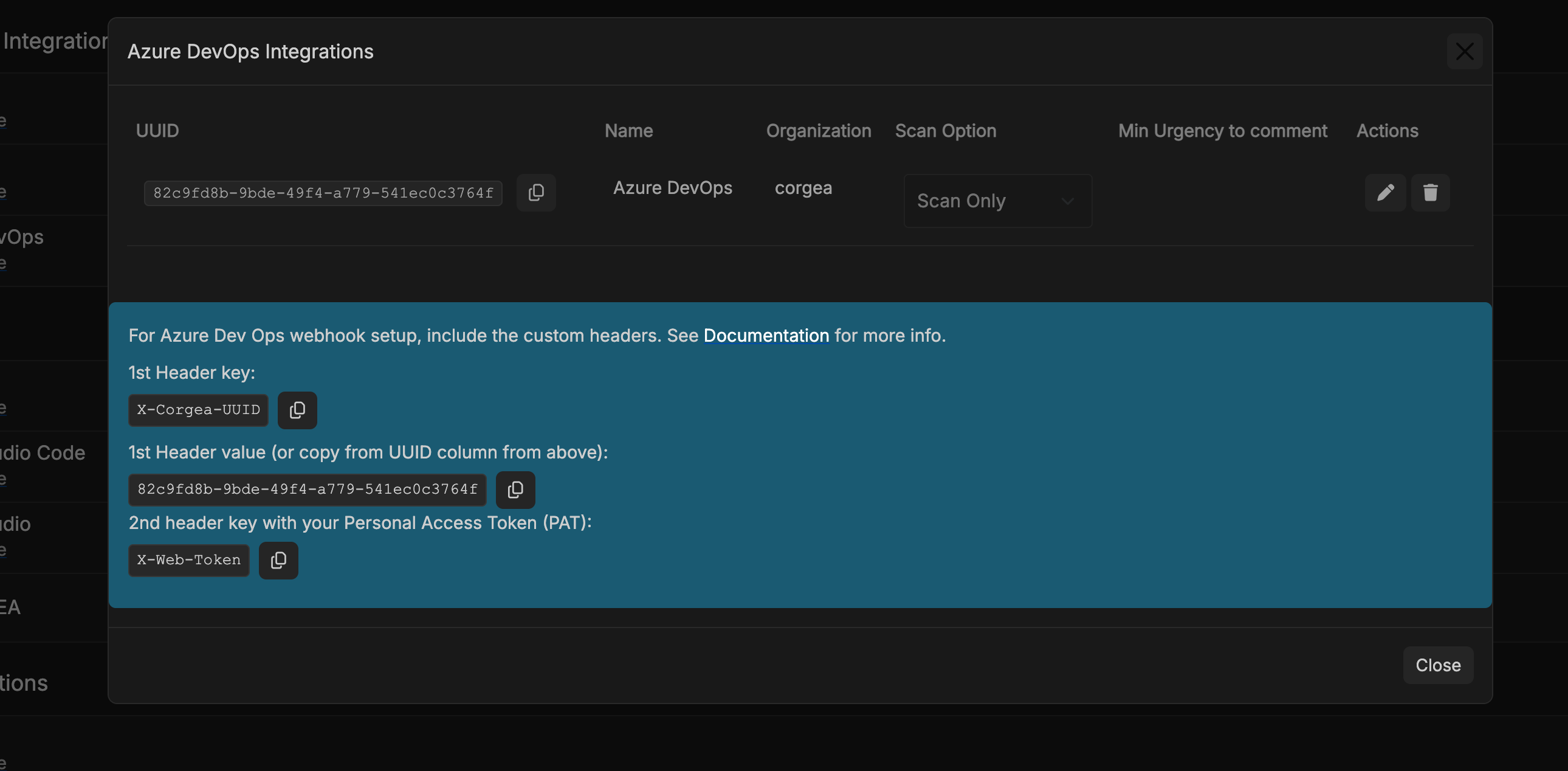

Return to the Azure DevOps Webhook configuration page and populate the headers section with: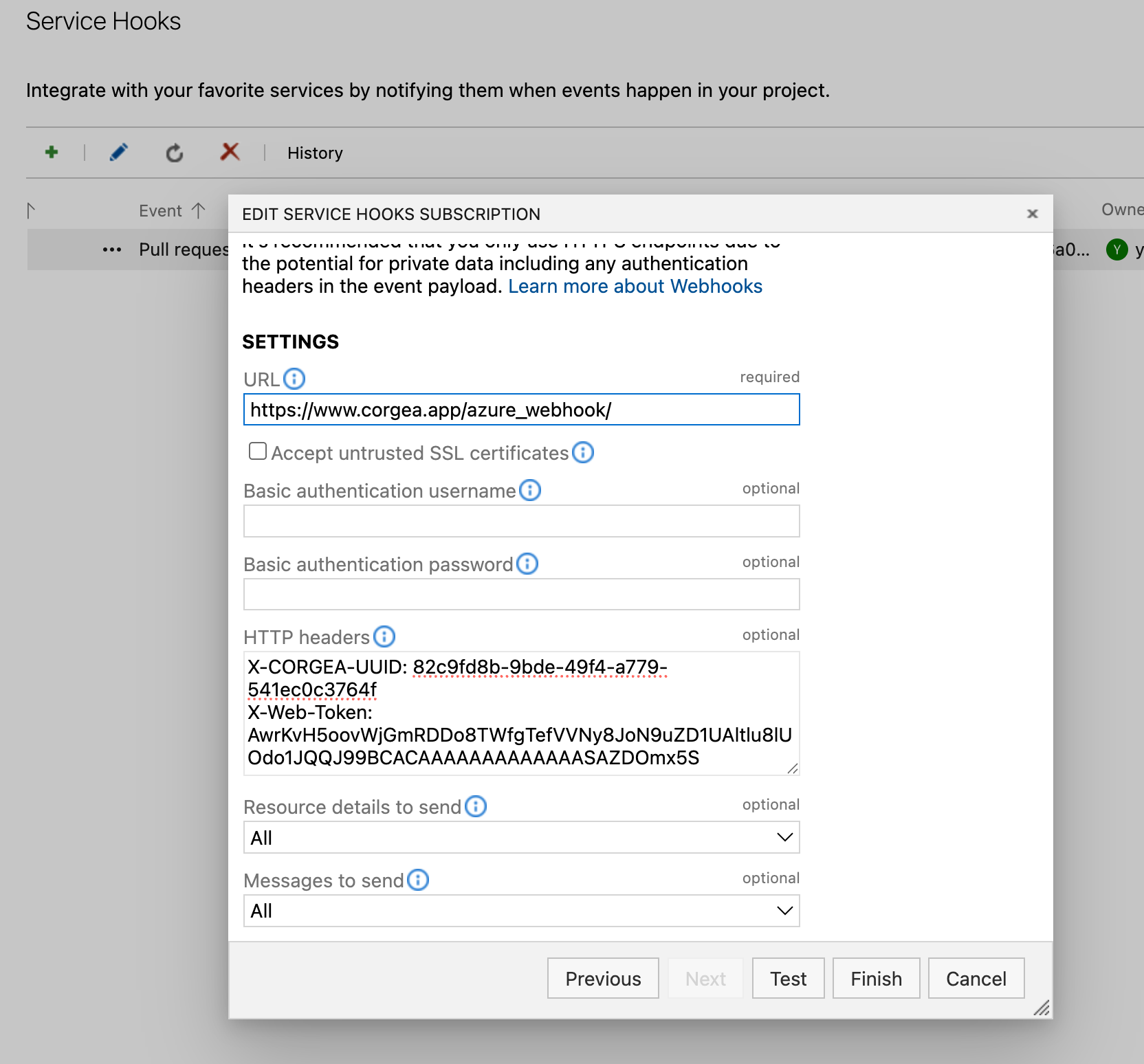
- X-CORGEA-UUID: (UUID value you copied)
- X-WEB-TOKEN: (the same PAT configured in Corgea)

Click “Finish” to save the configuration. Disregard the “Test” button as it may attempt to trigger scans for files you do not have access to.
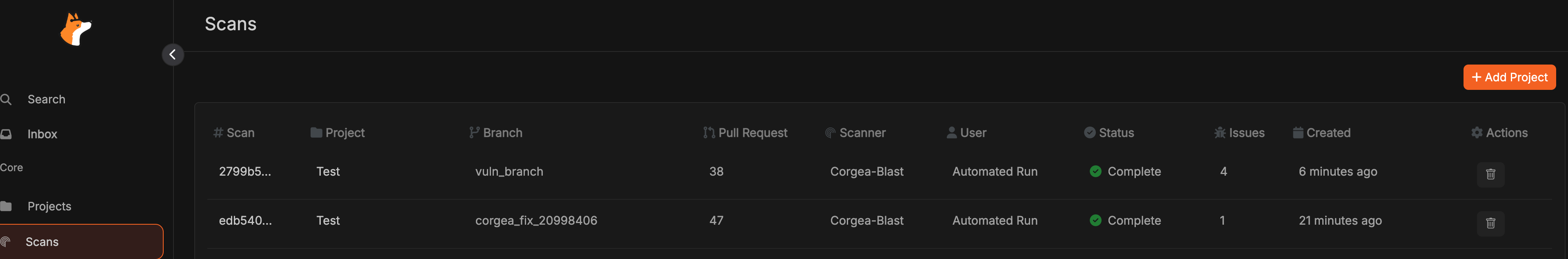
Validate the setup by creating a new pull request. A successful configuration will display a successful event in the webhook history and trigger a new scan on the Corgea Scans page at https://www.corgea.app/scans/.